Hacking Challenge: challenge hackers in a skill game
[Foreword: this is article number 2 of the new "hacks" series. Read here if you want to know more about this]
[Foreword 2: if you know me, you also know I usually don't use the term "hacker" lightly. I'm sure you will understand what I mean here without being offended, whether you are a (real) hacker or not ;-)]
In the latest years, also thanks to the fact that website creation has become a much easier and quicker task, the number of hacking challenges on the Internet has considerably increased. These websites usually consist of a series of riddles or puzzles, published by increasing difficulty; solving one of these riddles you can gain points or advance to higher levels where you can access some new resources inside the website. Riddles and puzzles, of course, are "tailored for hackers": the knowledge required to participate, in fact, covers a little bit of everything technical, from scripting languages to cryptography, from reverse engineering to Internet search techniques. Participating to these challenges is a very interesting experience, not only because it is instructive, but also because it allows you to network with other people with your same passion. And, after all, some narcisism doesn't hurt: most of the hacking challenges you can find around the Web also have a "hall of fame", inside which you can see the (nick)names of the hackers who reached the highest scores.
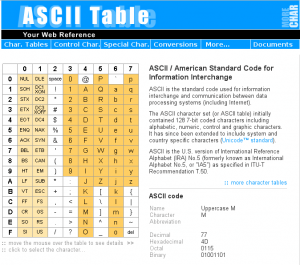
Figure 1: The website http://ascii-table.com provides an ASCII table with dec, hex, octal, and binary codes, together with a collection of tools to convert text in different formats. You'll be surprised at how much this can be useful for you.
Create new riddles
If participating to a hacking challenge as a player is really funny, letting people play your own challenge could be really awesome. Becoming "riddlers" is not particularly complicated from a technical viewpoint: everything you need is some time, together with lots of creativity.
The main idea is that the final answer to a riddle could always be summarized as a simple string of text: in the easiest case it could be a name, in the most complex it could become a (more or less long) sequence of apparently random characters. The easiest way to check if the string is right is to use it as part of the URL of the page containing the following riddle. You can ask users to manually type this URL inside their browsers or use some Javascript code to automatically generate it: if the answer is right the correct page will be loaded, otherwise the Web server will return an error message. More advanced methods to check riddle solutions involve the use of scripting languages (such as Perl, PHP, or Python) and passwords saved inside a file or a database.
The tools
Whatever your choice is, you will not have many problems in finding the Web space and the software you need to create your own hacking challenge. Actually, there are currently lots of free Web space providers available and many of them also give you the chance to run scripts or store your data inside databases. You can also practice by creating a test environment locally on your PC, using ready LAMP (Linux+Apache+PHP+MySQL) packages. For instance, XAMPP (http://www.apachefriends.org/it/xampp.html) is an Apache distribution that comes together with PHP, MySQL, and Perl: the installation procedure has been designed to be as simple as possible and in few minutes you'll be able to start experimenting with your site.

Figure 2: XAMPP is one of the quickest way to run a LAMP servers on your Windoze, Linux, or Mac computer.
Find inspiration
Before you build a new riddle you'd better gather some information, checking what has already been created and what in general you like most. The Web is full of hacking challenges you might get some inspiration from, however finding the one which might be more interesting for you is a riddle on its own. To help you in the choice, instead of searching for challenges on classical search engines you might better start from some more specific websites. Hackergames.net is a "historical" portal for this genre, with links to about 150 different challenges: for each of them you can find details such as the main language, a description, and a list of reviews written by users themselves. We Chall, instead, despite having links to less challenges, has introduced a whole new API-like communication system between websites; using that, it can aggregate scores from different challenges, allowing users to be listed into a global ranking which spans over many sites. Last but not least, keep an eye on all those sites (such as TheBlackSheep) that accept contributions from their own users, as they give you the chance to see your riddles published without requiring you to develop and maintain a website on your own.
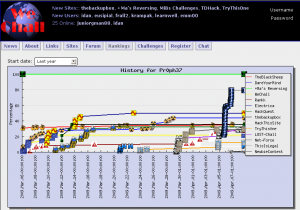
Figure 3: We Chall plots, for each user, all the progresses done in every challenge she has subscribed to.
Hacker psychology
The main rule in a hacking challenge worth this name is that there are no rules. If a solution to your riddle is not the one you had envisioned, well... that's a good thing: it means that who found it is more creative than you! Finding alternative ways to reach one goal is a very common hacker approach, so you shouldn't be surprised if, trying to find the solutions to your riddles, somebody tries to exploit your system vulnerabilities. So, here are some suggestions to keep your challenge as funny as possible, both for your players and you:
- check how secure your scripts are, in particular against the most common types of exploit (such as SQL injection, if you save data inside a database);
- do not rely on "security by obscurity", making the security of your website depend on the secrecy of some pieces of information: give for granted the fact that they will be discovered sooner or later and act accordingly. For instance, do not keep all the solutions to your riddles in clear but rather encrypt them, so that whoever finds them will have to sweat a little more to get to the next level;
- one of the simplest, but at the same time effective way to crack a short password is bruteforcing. So, use secret strings which are long and difficult to bruteforce, and make it clear for everyone: this way, users will avoid bruteforce finding it unuseful (and save a lot of your bandwidth);
- if you are good with programming, you can intentionally leave some bugs in the system so that users will be able to exploit them enabling new features inside your site, such as a secret forum or a list of hidden resources: there's no better incentive for hackers than the possibility of shaping a system according to their own will!
- if you receive a message from a user warning you about a vulnerability, consider it as a great privilege: instead of defacing you, they have sent you a constructive contribute! Try to learn more from that, correct the bug and document everything, so that all the other users will be able to learn something new from your error and from the ability of who discovered it. Finally, challenge everyone to find others: this will make the game even more interesting.
Telnet Email: access your email without a mail client
[This is article number 1 of the new "hacks" series. Read here if you want to know more about this]
In the beginning was the command line. Then, the evolution of software saw more and more complex graphical applications, able to abstract from low-level machine operations and make work much easier for the end user. All of this, of course, had a price: the loss of control. But we are not common users... and if there is one thing we want it is having control over what happens on our computers!
Let's think, for instance, about email: in most of the cases we can access our
mailbox with a browser, however only through an interface which has been already defined by our provider; this interface often contains advertisements and forces us to stay connected while we read our mails. We can configure an email client and make it download our messages from the server, however this choice has its drawbacks too: what should we do, for instance, if the computer we are using is not ours? The solution to this problem is very easy: let's come back to the origins, manually executing all the operations that an email client automatically performs whenever it downloads our emails from a server. The only tool we need is available on any computer: its name is telnet and it can be called from the command line (that is from Windows "command prompt" or from MacOSX and Linux Terminal). The data we need to know in advance are just the address and the port of our mail server, which are usually specified by our providers within the howtos for mail client configuration, together with our account's login and password.
Mail servers
Mail servers available on the Internet usually belong to one of two different
categories: outgoing or incoming mail. The former ones usually use SMTP (Simple Mail Transfer Protocol) and are accessed to send messages, while the latter ones use either POP3 (Post Office Protocol 3) or IMAP (Internet Message Access Protocol) and are the ones we will describe more in detail in this article, as they are used to download messages from a mailbox to our computer. Most of the times mail server addresses are built starting from your email address domain name and adding a prefix witch matches the protocol used: for instance, for gmail.com emails the outgoing server is called smtp.gmail.com, while the incoming ones are called pop.gmail.com and imap.gmail.com. A last parameter you have to specify to connect to a server is the port: the default values are 110 for POP3 and 143 for IMAP.
Let's keep things private
Before starting, however, you have to be aware about the following: every time you connect to one of the ports we just described, your data will be transferred in clear. This means that anyone would be able to read what you write just by sniffing the packets that are sent over the network. Luckily, some mail servers also accept encrypted connections (see below): in this case, the default ports are 995 for POP3 and 993 for IMAP. Finally, it is good to remember that all the information you send, independently from the fact that you are using an encrypted connection or not, are shown on the screen, so you'll better check that nobody's near you before entering your password...
NOTE: for those mail servers which, like gmail, require an encrypted connection, you can't just have a simple telnet connection. However, you can use the openssl program (available here). The syntax to connect is the following:
openssl s_client -connect <server name>:<port>
For instance:
openssl s_client -connect pop.gmail.com:995
Connect to the server
After you have chosen the connection type and verified you have the correct data, you can finally connect to your mail server using telnet. To do this you first have to open a terminal: from the Start menu in windows, select the Run option, write the "cmd" command, then press Enter; if you have a Mac, choose the Terminal application from the folder called Application/Utilities; in linux you can find it in the Utilities or Tools section (or you can have a full screen terminal by pressing the keys CTRL+ALT+F1). Once the terminal is open, you can connect to the server by writing
telnet <server address> <port>
For instance:
telnet pop.mydomain.com 110
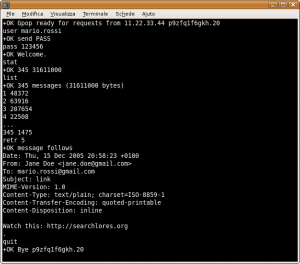
If the connection is opened correctly the server replies saying it is ready to
receive commands. Images show the main commands you can run on a POP server and below you can find different examples of connections both to POP and IMAP servers. IMAP servers are a little more complex than POP (for instance, every command has to be preceded by a tag containing an incremental value), however it is much more powerful at the same time, as it allows you to manage your mail in folders and mark messages with specific flags. All you have to do now is experiment with this new tool, maybe a little spartan but with no restrictions imposed by proprietary interfaces, and find new ways to manage your email with telnet.
POP3
The POP3 protocol is quite easy and follows the specs which appear inside RFC1939. Here's a list of the main commands:
- USER <username>: specifies your email account's login
- PASS <password>: specifies (in clear) your email account's password
- STAT: shows the number of messages in the mailbox and the total space they require
- LIST: shows a list of messages with their size
- RETR <message id>: shows the message identified by "id"
- TOP <message id> <n>: shows the first <n> rows of the message
- DELE <message id>: deletes the specified message from the server
- RSET: resets all the DELE operations previously performed (within the same session)
- QUIT: quits the POP3 session and disconnects from the server
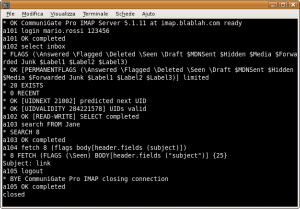
IMAP
The IMAP protocol follows the specs of RFC3501 and is far more complex than POP3. For this reason, instead of a list of commands we just show a session example, suggesting you to check the RFC or to search for "IMAP and TELNET" to get more details.
01 LOGIN <login> <pass> authenticates on the server 02 LIST "" * shows the list of available folders 03 SELECT INBOX opens the INBOX folder 04 STATUS INBOX (MESSAGES) shows the number of messages in the current folder 05 FETCH <messagenum> FULL downloads the header of the specified message 06 FETCH <messagenum> BODY[text] downloads the body of the specified message 07 LOGOUT disconnects from the server
New “hacks” series
It all started last winter, when a couple of old friends asked me if I wanted to help in writing articles for an Italian magazine. The zine was targeted at young people willing to learn something more about what is going on inside their computer: some would call them wannabe hackers, I'd prefer to think about them as potential reversers ;-)
Why did I accept this work? The reasons are many, including the deep respect I have for these friends, some nostalgia of good old times, the fact that the magazine has no ads, and finally the right to redistribute my articles online.So here they are, a collection of introductory texts that I hope will be useful for someone. If you are already an expert you will probably find nothing interesting here, but I like to think that few people really are as expert as they think.. ;)
So, how does it work? Well, I don't have much time so I usually write a very short article each month. The original article is always in Italian, so I have to translate it (any help is more than welcome!). I already have a buffer long enough to keep you busy for a while, so here is my plan: one article every other Sunday for some months, then we'll see (yeah, this does not sound like a very detailed plan :)).
Shall we start?