Escape
From IT
This short story aims to explain how to avoid being tracked on the web or through the use of new technologies. In fact, nowadays every move through the web or in real world is recorded somewhere. To make reading more enjoyable the text is presented in story form.
Before starting the reading, the following assumptions must be taken into consideration:
- The story is invented and inspired by the family of Al Capone: which was a U.S. criminal, of Italian origin, considered a symbol of American gangsterism and the crisis of legality that the U.S. had to face during the twenties.
- The book Little Brother has been the source of inspiration for this story. I kindly invite the reader to read it.
- All the information comes from the Internet. Because the author of this text simulated a real situation.
- The simulation of different software described has been done by the author of this text.
Contents |
Chapter 1
Christmas 2011, the day I decided to run away
Christmas lunches and dinners: we are forced to invite relatives that we never see, except at Christmas. And often, the Christmas lunch becomes an excuse to see resurgence old conflicts that seemed dormant. My secret was to take a Zen attitude and to remember that the deeper meaning of Christmas is to give hospitality to those who live alone or far away and maybe they wants to see us more. But often my attitude was not enough, as well as the attempt to settle with care the seating plan. In fact, it must be admitted, my family was not exactly the most common one. My great uncle Al, Alphonse Gabriel "Al" Capone, was a well-known Italian-American gangsters and my whole family turned around the world of criminality. Until the activities were conducted without the help of the Web, their influence was limited to the city of Chicago, but since Internet was invented the organization was infiltrating in many American cities. My parents were very worried for my safety. In fact, since I became adult, my uncle insisted in let me be part of the family “activities”. So, in December 2011, my parents and I decided it was time to leave the United States. The day chosen was December 25. During the Christmas lunch, when the family was gathered around the supper table, I left.
Chapter 2
The departure
The bag was ready, the life savings of my parents were inside, the false passport created by my cousin Calogero was in my pants, as well as air ticket to Europe. While the capon stuffed with chestnuts was served, I got up from the table. And, I left.
The measures introduced to improve the level of security in customs and especially in airports - subsequent to the dramatic events of 11 September 2001- had led to the creation of the electronic passport. My cousin, Calogero, a nerd with incredible talent, had contacted his friend Phil, who was part of a group of hackers called THC (The Hacker's Choice). His friend and him put in place my documents. The falsification of the passport had proved to be a fairly simple task, even understandable for me. In practice they inserted a smart card that integrated an RFID chip reprogrammed. Before that day I did not know what it was. So some days before I googled it and Wikipedia explained me that “Radio-frequency identification (RFID) is a technology that uses radio waves to transfer data from an electronic tag, called RFID tag or label, attached to an object, through a reader for the purpose of identifying and tracking the object. Some RFID tags can be read from several meters away and beyond the line of sight of the reader”. Several meters... I was worried... So I decided to continue my search in order to understand if I was in danger. Fortunately I discovered that exists two types of RFID: active and passive ones. The active RFID “has a transmitter to send back information, rather than reflecting back a signal from the reader” and “most active tags use a battery to transmit a signal to a reader. However, some tags can gather energy from other sources. Active tags can be read from 300 feet (100 meters) or more, but they're expensive (typically more than US$20 each). They're used for tracking expensive items over long ranges. For instance, the U.S. military uses active tags to track containers of supplies arriving in ports.” (RFiD Journal. GLOSSARY OF RFID TERMS: Active tag.). I did not feel reassured until I discovered the existence of Faraday protection bags for e-passport security: which of course I immediately bought.
After its implementation, the passport was checked by a friend of Phil in an airport and seemed to work. But even if the document issue seemed to be solved, my fears - regarding the check-in - were not reduced. In any case, the next issue to solve was the facial and gait recognition.
In fact, the activities of my family included the search of enemies and the identification of family members in case of problems. Uncle Alfonso had a big team of computer scientists working for him. And, on a secret server all the information about family, friends and enemies were collected, including of course mine. Moreover they were able to view images related to the airport webcam. I had to find a way to not be recognized.
The first solution was to cancel my card from the database. But this was too dangerous. If I asked someone it would be suspicious and if I had manipulated the database someone would surely notice it. The only solution was to make myself invisible to computer systems. How? Let’s talk about facial and gait recognition.
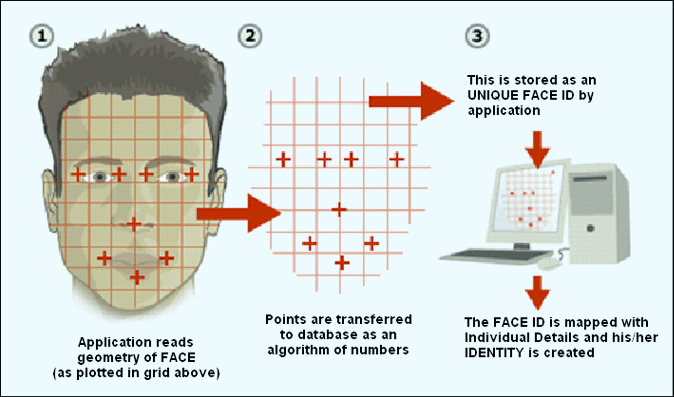
Again, I submit myself to a session of Google self-learning, i.e. I googled facial and gait recognition. It was amazing. I discovered that facial recognition researches started in 1989, when a brilliant professor, Dr. Eng. Teuvo Kohonen, interested in pattern recognition and informatics decided to apply his theories to this field. In more than twenty years of course things have changed. Today you can really recognize people from a video or image and be sure of its identity. You can even make predictions about his future appearance! But how does it work? Every face is different and characterizable with distinguishable landmarks, called nodal points, it means the different peaks and valleys that make up facial features. There are many software dedicated at this practice but in general we can say that each human face has approximately 80 nodal points. The data relating to a face - Distance between the eyes, width of the nose, depth of the eye sockets, etc. - are represented numerically in a vector or in a matrix. The image below shows the process of Face ID creation.
And now, how avoid recognition? Again, internet gave me the response. I found a very interesting video on Youtube and I strongly suggest to you to look at it before continuing the reading.
Sunglasses? I have it. Hooded sweatshirt? of course! Gait recognition now.
Few months before my departure I read an interesting book titled “Little Brother”. Which tells the story of a boy, with excellent computer skills, who knows - among other things - how to avoid gait recognition.
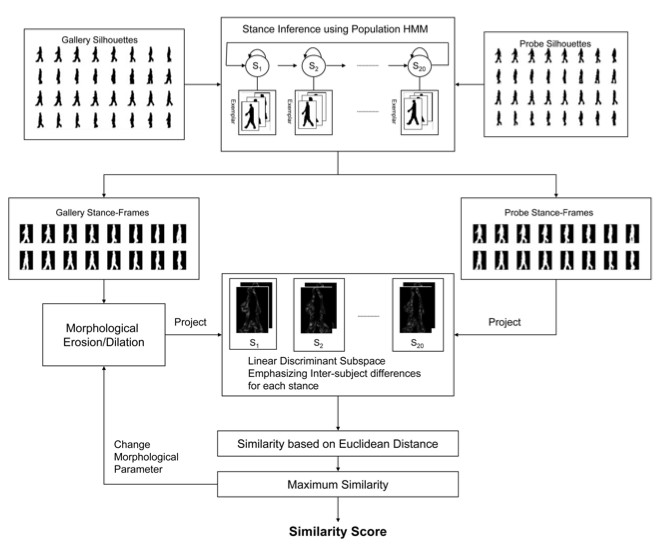
In fact, as for facial recognition, the systems can fail if some variables affect recordings. As mentioned above, my family already had a sample of my posture. So the only thing to do was to "disguise" my nature. First of all the database contains samples of walking silhouettes corresponding at each known person. And, when you search for someone, you compare the new sample with those in the database. The closer the two sets are, the higher is the probability to recognize someone. See following schema.
These recognition systems are becoming more and more powerful, because the population is more and more video surveilled. But I had the solution in my hand. Really, in my hand: a handful of sand. No, It is not a metaphor, my idea was to buy a new pair of shoes and put it inside some sand. The completely new sole in combination with sand would have caused a change in my posture. As a result, the systems would not be able to recognize me.
I was ready. At least I thought. In any case I went to the airport and I took the fly.
Chapter 3
How to contact my family
I arrived in Rome a dreary January morning. There, an old friend of Dad was waiting for me. I really missed the family: so I had to find a way to contact them and tell them that I was fine. It was time to pull out my computer from my bag.
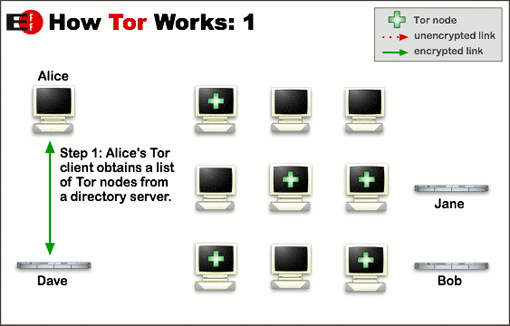
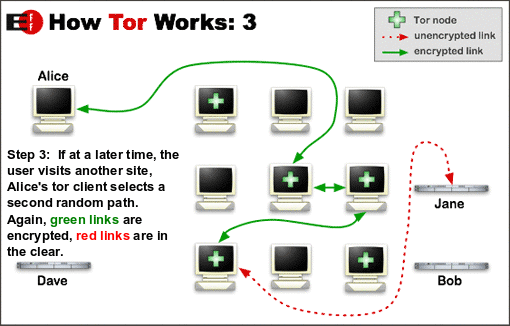
Instead of completely erase all my data from my computer, I discovered that to ensure my privacy (I was a Mac user) I could just go to System Preferences> Accounts , create a new administrator user and delete the previous one. This process erased all my personal information - i.e passwords, preferences, firefox history, etc. - but not the programs. I should not download them again. The only program which of course I had to make sure that I had was Tor. Tor (The Onion Router) is an anonymous Internet communication system based on second-generation onion routing protocol. What does it mean? That through Tor you can browse internet anonymously. The software is free as well as its usage.
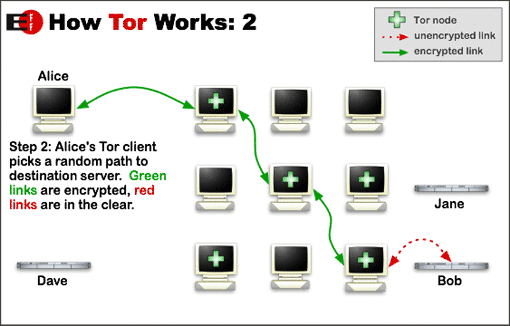
The TOR network, which stands for The Onion Routers, is based on a set of nodes, called relay, consisting of intermediate servers through which our data pass before arriving at their destination. In practice, our data - before arriving at the website server required - pass in these nodes in a random way and always using a different path. Moreover the network change the path of our data automatically every ten minutes. The types of servers used for this network, called onion routers, are managed by volunteers, which allow the anonymous outgoing traffic and the creation of anonymous hidden services. Why are they called onion? No, it’s not because they make you cry. It’s because our packages are encrypted with a double key in every node, so the transaction of packages from router to router is more safe. So, at each step is added a layer and each package become like an onion!
It must be admitted that the system is quite ingenious. But the first time I used it I was a frustrating experience. Not because Tor is difficult to use (in fact, it's easy) but rather for its slowness. In fact, the continuous encryption and decryption of packets associated with the redirection, has its drawbacks, i.e. time. But, to be invisible repaid me. Although I had decided to use TOR to contact my parents I did some internet searches on “How to surf anonymously without a trace”. And, I found several other programs but non of them seemed to be reliable as TOR. But the most extraordinary and unexpected discovery I made was in an online newspaper article. What did the article tell?
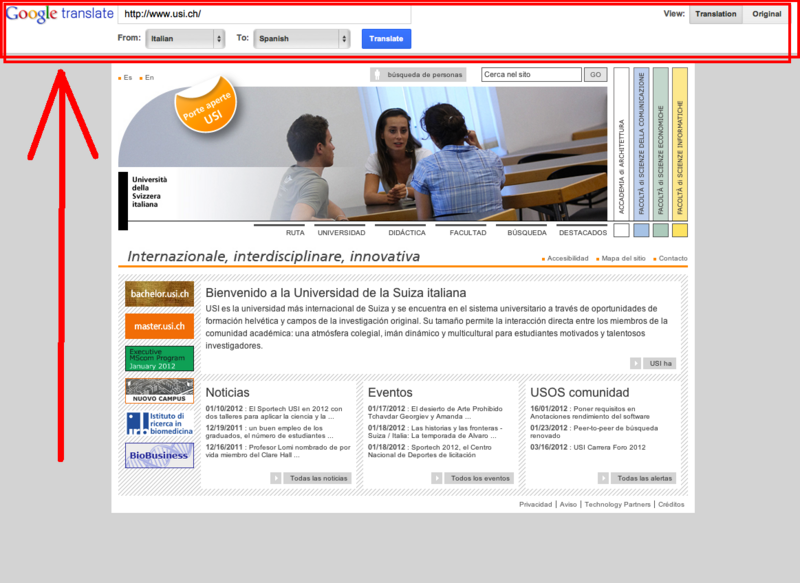
The article explains that if you put in the box of Google Translate an URL, the system translates the entire page and, as a result it gives you the entire page, including the layout. What is just amazing is the fact that you can continue to navigate inside the website as you were using a browser. It’s like use a browser inside a browser. Therefore you are seen as a user visiting the Google translate page and not as a visitor of the specific page, because you're just translating it!
Now I was ready to contact my family on a secure line. With my computer in the arm I headed to an internet cafe, I ordered a giant soft drink and I sat at a table.
Hi mom, I miss you
When I was still in the USA, I was not sure I could connect from my PC safely also in Europe. Who could assure me that I would found free wifi? So I brought with me a USB key with Ultrasurf installed on it. This software is amazing, first because ensure privacy, security and freedom and second because is a self contained program. It means that it doesn’t require installation! You just open it and it runs. On every Windows 7/Vista/XP computer. Of course I had a mac. But who knows what can happen? In any case my mother needed it. In fact in order to keep in touch we had decided that I would send to her mails and she would reply on a blog. Unfortunately his informatics skills did not allow us other solutions. In any case my mother needed it. In fact in order to keep in touch we had decided that I would send to her mails and she would reply on a blog. Unfortunately his informatics skills did not allow us other solutions. Sitting in that bar, with the mild sunshine of January, I opened my terminal. I connected with telnet I filled out the required fields and I sent the first mail to my mother. "Mom I'm okay, I miss you" 10 minutes later on a small blog created with WordPress a post appeared. "We miss you too much". The adventure of being invisible on the Web had begun.
Bibliography
- Doctorow Cory. 2007. Little Brother.
- Homeland Security NewsWire. New facial, gait recognition software to be integrated in CCTVs. February, 2009.
- KAMRUL HASAN, NAZRUL ISLAM MONDAL, NAFISA TARANNUM, TANVIR AHMED CHOWDHURY. RECOGNITION OF FACIAL PATTERN BY MODIFIED KOHONEN’S SELF ORGANIZING MAP (MKSOM) AND ANALYZE THE PERFORMANCE.INNOVATIVE APPLICATIONS OF INFORMATION TECHNOLOGY FOR THE DEVELOPING WORLD (pp 399-406)
- RfiD Journal. LOGISTICS EXPERT VIEWS. Readers That Sense Distance
- Masaki Yamazaki, Yen-Wei Chen and Gang Xu. Human Action Recognition Using Independent Component Analysis
- Paraben's StrongHolg. PROTECT YOUR RFID PASSPORT.
- RFiD Journal. GLOSSARY OF RFID TERMS: Active tag.
- Anonimouse. AnonWWW.
- TECNOLOGICA-MENTE. Un passaporto elettronico falsificato in 5 minuti.
- Tor. Anonymity Online.
- Zongyi Liu and Sudeep Sarkar. Improved Gait Recognition by Gait Dynamics Normalization. IEEE TRANSACTIONS ON PATTERN ANALYSIS AND MACHINE INTELLIGENCE, VOL. 28, NO. 6, JUNE 2006
Interesting links
- How to know your ip address.
- The Telegraph. Philip Johnston. Mind how you walk. It could be a crime.
- 11 Great Hidden Things Google Can Do That You Should Know.
- Ultrasurf. Self contained software for anonymous surfing and browsingVideo: How to avoid Video Surveillance Camera and Avoid Facial Recognition.
- The Hacker's Choice